Can cloud mining solutions for Bitcoin offer greater decentralization?
Decentralization is one of the key characteristics that define Bitcoin and its vision of finance. While Bitcoin’s Proof of Work consensus algorithm has proven to be highly secure and robust, there have also been a few downsides that have hindered Bitcoin’s growth. The mining community keeps the network alive, however, increased levels of centralization can be found when it comes to mining pools.
In the latest episode of the Untold Stories podcast, Marco Streng, CEO of Genesis Mining discussed some of the key aspects of cloud mining and the ever-increasing need for better transparency within the operations. Streng pointed out that as the crypto industry grew and matured, unfortunately, the levels of transparency has dwindled.
“In crypto, the secrecy plays an important role and because there’s so much money involved, but I guess if he’s [mining-operators] serious, they should disclose the people behind them, the team.”
– he said.
He went on to add that in the ideal scenario the ecosystem ought to be trustless:
“We basically want to find ways that less trust is needed at least. And that is not an easy task. There are many ways how more disclosure doesn’t necessarily really tell you anything more about whether it’s a bounded operator or not”
– he said
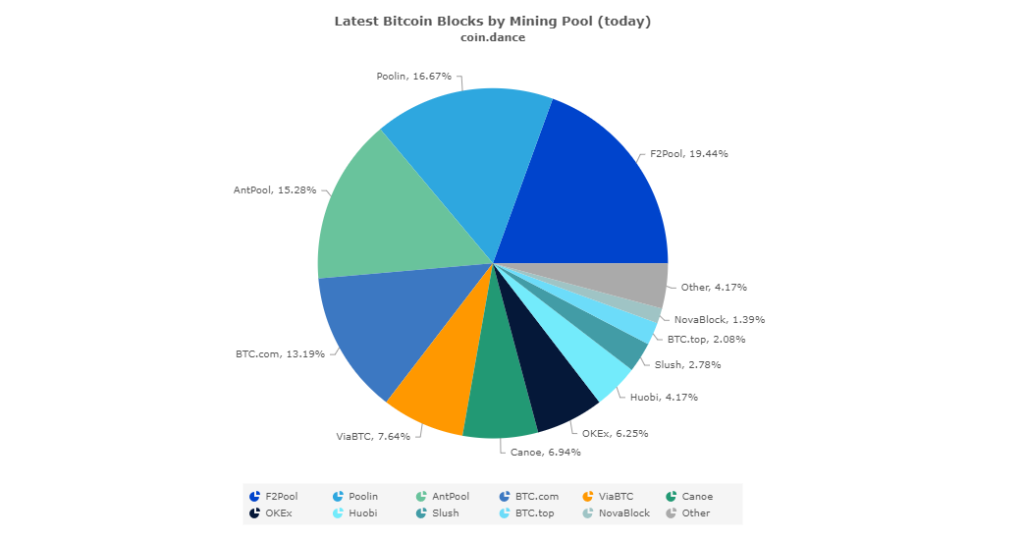
According to data regarding the mining pools that sustain Bitcoin, the majority continue to be based out of China, and as Bitcoin grows so have the scale of mining operations for the top players. This also highlights the growing concern that the world’s largest cryptocurrency that popularized the term decentralization is being sustained by an increasingly centralized network of miners.
While cloud-based Bitcoin mining operations have a long way to go in terms of security and authenticity, Streng pointed out that for such an ecosystem to be set-up and sustained greater measures can be implemented to give miners total control of their mining activity:
“We really want to have at one point a completely trustless mining cloud mining operation. But that is really hard…Go on hardware level and use encryption on the hardware level, that then makes it possible so that we as operators, can’t even control the machine and the user that is remotely connected has more control of the machine.”
– he said.
Source: eng.ambcrypto.com


